This post is also available in: Russian
Apple’s DRM technology is called FairPlay. Its inner workings are kept secret and it cannot be licensed for use with stores other than iTunes and with non-Apple devices. The rationale for this decision can be found in Steve Jobs’ article:
The second alternative is for Apple to license its FairPlay DRM technology to current and future competitors with the goal of achieving interoperability between different company’s players and music stores. On the surface, this seems like a good idea since it might offer customers increased choice now and in the future. And Apple might benefit by charging a small licensing fee for its FairPlay DRM. However, when we look a bit deeper, problems begin to emerge. The most serious problem is that licensing a DRM involves disclosing some of its secrets to many people in many companies, and history tells us that inevitably these secrets will leak. The Internet has made such leaks far more damaging, since a single leak can be spread worldwide in less than a minute. Such leaks can rapidly result in software programs available as free downloads on the Internet which will disable the DRM protection so that formerly protected songs can be played on unauthorized players.
For the same reason other important players in this field Flash Access and Windows Media RMS both are closed technologies not available for licensing.
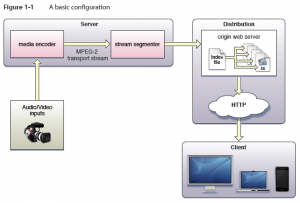
Apple has its own implementation of HTTP Streaming technology based on IETF Internet-Draft. It does not support DRM as stated in developer documentation. However, media can be encrypted and key access can be limited using HTTPS authentication.
Media files containing stream segments may be individually encrypted. When encryption is employed, references to the corresponding key files appear in the index file so that the client can retrieve the keys for decryption.
When a key file is listed in the index file, the key file contains a cipher key that must be used to decrypt subsequent media files listed in the index file. Currently HTTP Live Streaming supports AES-128 encryption using 16-octet keys. Wowza supports the same encryption technology.
The media stream segmenter available from Apple provides encryption and supports three modes for configuring encryption.
The first mode allows you to specify a path to an existing key file on disk. In this mode the segmenter inserts the URL of the existing key file in the index file. It encrypts all media files using this key.
The second mode instructs the segmenter to generate a random key file, save it in a specified location, and reference it in the index file. All media files are encrypted using this randomly generated key.
The third mode instructs the segmenter to generate a random key file, save it in a specified location, reference it in the index file, and then regenerate and reference a new key file every n files. This mode is referred to as key rotation. Each group of n files is encrypted using a different key.
You can serve key files using either HTTP or HTTPS. You may also choose to protect the delivery of the key files using your own session-based authentication scheme.